From Past to Future: How Data Breaches Evolved, Their Costs, and How to Mitigate Risks

An estimated 4000 cyberattacks occur daily, with most being data breaches, leaving personal information exposed and vulnerable
1.0.0.21resigned1
Have you ever experienced getting your data leaked or exposed? According to cybersecurity company Astra, an estimated 4000 cyberattacks are launched each day, the majority of which are data breaches. Data breaches occur when your personal data gets accessed by someone unauthorized to do so, which leaves your information exposed and vulnerable.
Data breaches are often costly and can happen to both private entities and companies. Cybercrime Magazine’s report found that cybercrime, which includes data breaches, costs $8 trillion globally. Understanding how they happen plays a big part in preventing them.
This article will take a closer look at how data breaches have grown and evolved, the impact compromised data can have on your systems, and how to, ultimately, mitigate data breaches if you encounter them.
A Historical Overview of Data Breaches
When you think about data breaches, you usually associate them with digital platforms and technology. However, data breaches have been around as long as keeping records and private files have. Someone getting a glimpse of your medical papers without your consent, for example, counts as a data breach.
Data breaches were first recorded in the 1980s, becoming more common throughout the 1990s and 2000s as technology progressed. One of the earliest recorded digital breaches occurred in 1984 when German hacker Karl Koch infiltrated U.S. military networks, exposing vulnerabilities in early computer systems.
The Evolution of Data Breach Methods

Infecting 50 million computers and causing $15 billion in damage, the ‘ILOVEYOU’ worm highlighted the role of email in cyberattacks
1.0.0.21resigned1
In the 1990s, as businesses transitioned from paper to digital records, cybercriminals began exploiting these new systems. The proliferation of email introduced avenues for attacks, with the “ILOVEYOU” worm in 2000 infecting over 50 million computers and causing approximately $15 billion in damages, as noted by the Katz School of Science and Health.
The 2000s saw a surge in malware and phishing attacks, coinciding with the rise of mobile usage and online transactions. By 2007, new malware instances had escalated to 5 million annually, up from tens of thousands in the early 1990s.
In the 2010s, cyber threats became more sophisticated, with advanced persistent threats (APTs) and targeted phishing, such as spear phishing, becoming prevalent. Notably, the “WannaCry” ransomware attack in 2017 affected over 200,000 computers across 150 countries, resulting in an estimated $4 billion in losses.
As technology advances, so will data breach methods. As such, legislation to protect private information has been in the works. HIPAA, for example, was developed to safeguard patients’ medical information and ensure confidentiality. While more sophisticated data breach methods are expected, stronger legal protections for data will also emerge to safeguard personal information.
Biggest Data Breaches in History
Data breaches are devastating, impacting millions of users. Here are nine of the biggest data breaches that happened over the past decade.
| Company | Impact of Data Breach | What Happened |
| Facebook (April 2019) | 533 million users | Facebook data was compromised and leaked, with viewers able to access over 533 million records of chats, comments, and engagement on the app. |
| Cam4 (March 2020) | 10.88 billion users | Cam4 was a video streaming site for adult videos, and its 2020 leak exposed the following details of members:
|
| Sina Weibo (March 2020) | 538 million users | Sina Weibo is a popular Chinese social media platform that had its data compromised in 2020. The data was sold on the Dark Web for $250, and contained the following details:
|
| LinkedIn (June 2021) | 700 million users | LinkedIn had its data shared and sold on the Dark Web after a hacker scraped its API, exposing users’:
|
| Twitch (October 2021) | Roughly 7 million users | Twitch’s user base was exposed in a data breach. Developers discovered this after an anonymous source shared a torrent link with over 100 GB of user information posted on 4chan. |
| National Public Data (2023) | 170 million users | Around 2.9 billion records of the fraud prevention service were exposed and leaked into the Dark Web:
|
| TicketMaster Entertainment LLC (2024) | 40 million users | TicketMaster was infiltrated by hackers exploiting a kink in their customer service system, exposing millions of users’ data. |
| Change Healthcare (2024) | 190 million users | Ransomware gang BlackCat exposed 6 TB of Change Healthcare’s data, disrupting payment and billing activities in the process. This attack is considered one of the most devastating data breaches in U.S. healthcare history. |
| Tencent (2024) | 1.4 billion users | Chinese conglomerate Tencent was hacked in 2024, with the attacker making user data freely available in the public domain. The following user information was compromised:
|
Sources: CSO Online and Upguard
Current Data Breach Statistics
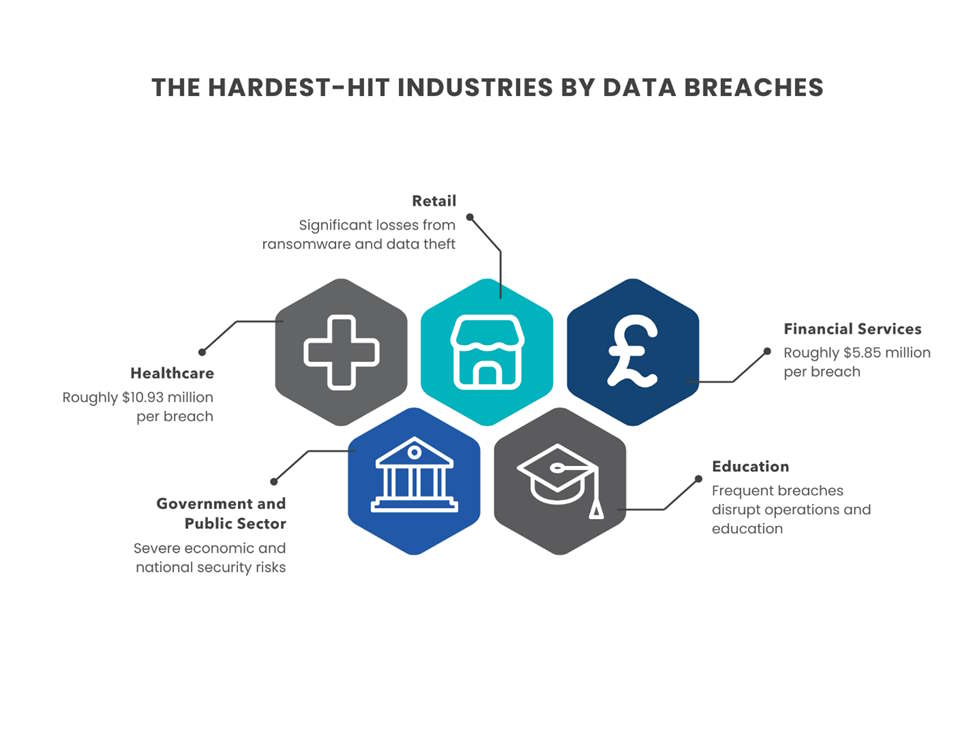
Cyberattacks have evolved into a major threat across industries, with some sectors suffering more severe financial and operational consequences than others. Tech Business News identifies healthcare, financial services, retail, government, and education as the most targeted mostly because of the volume and sensitivity of data.
| Industry | Impact |
| Healthcare | The highest cost of cyber attacks at roughly $10.93 million per breach |
| Retail | Varies (Significant losses from ransomware and data theft) |
| Financial Services | Roughly $5.85 million per breach |
| Government and Public Sector | Government systems face severe economic and national security risks |
| Education | No specific cost was reported, but frequent breaches lead to operational disruptions and stall students’ education |
Source: IBM
Global and Regional Data Breach Facts and Statistics
- According to the ITRC Annual Data Breach Report, 2024 saw 3,158 data breaches
- Victim notices of data breaches grow by 211% year-over-year, highlighting the impact of compromised data on users
- Majority of data breaches come from cyber attacks, but human error is the second leading cause of having your data compromised
- According to Time, there were six breaches in 2024 that resulted in the leak of millions of users’ private information
- Astra, a digital security company, notes that 45% of data breaches are cloud-based
- Cybersecurity company Surfshark found that an email address can be breached an average of 3 times
- Cybercrime is projected to cost the global economy $10.5 trillion by 2025
- Research by IBM discovered that 40% of data breaches were caused by a third party, while 33% of data breaches were caused internally
- According to Statista, there are 4.62 million accounts around the world that are breached quarterly
| Country | Percentage of Organisations That Lost Sensitive Information (Data by Statista) |
| South Korea | 77% |
| Canada | 61% |
| France | 58% |
| Germany | 57% |
| Sweden | 54% |
| United States | 52% |
| Spain | 46% |
| Netherlands | 45% |
| United Arab Emirates | 45% |
| Brazil | 40% |
| United Kingdom | 39% |
| Australia | 39% |
| Japan | 34% |
| Singapore | 32% |
| Saudi Arabia | 31% |
| Italy | 27% |
Trends in Data Breaches
Data breaches continue to evolve, leveraging advanced technologies, exploiting human vulnerabilities, and adapting to new security measures. Understanding these trends is essential for businesses looking to strengthen their cybersecurity posture and mitigate risks effectively.
Emerging Threats and Attack Vectors
Cyberattacks have moved beyond traditional phishing and malware-based breaches. According to Google Cloud, attackers now use machine learning algorithms to mimic executives’ voices or generate convincing fake identities to bypass authentication systems. More sophisticated phishing attacks are also fuelled by breaches such as the “Mother of All Breaches” that exposed billions of credentials. Here are the online industries that were most impacted by phishing attacks in 2024.
| Online Industries | Attack Percentage (Data from Statista) |
| Social Media | 30.5% |
| SaaS | 21.2% |
| FinTech | 13% |
| Retail | 8% |
| Payments | 5.8% |
| Telecommunications | 4.9% |
| Shipping | 3.1% |
| Travel | 2.6% |
| Cryptocurrencies | 2.4% |
| Miscellaneous | 8.5% |
Another growing concern is supply chain attacks, where hackers infiltrate trusted third-party vendors to access multiple organisations at once. In 2023, Statista noted that supply chain breaches increased to 242 attacks from 115 in 2022, affecting businesses across different industries. Ransomware remains a dominant threat, with cybercriminals targeting backups and cloud storage to make recovery nearly impossible without paying a hefty ransom. According to Cybersecurity Ventures, it could cost $10.5 trillion in 2025.
Impact of Technological Advancements on Data Breach Management and Attacks

40% of data breaches occur due to data being accessed and stored across multiple devices and locations
Researchers have found that while cybersecurity technologies have advanced, attack methods have evolved as well, heightening the need for more robust security measures. The shift toward cloud-based infrastructure and IoT devices has expanded the attack surface, making it easier for hackers to find weak entry points. The widespread adoption of remote work and hybrid office models has also increased vulnerabilities, as more employees access company networks from personal devices and unsecured Wi-Fi networks. According to IBM, 40% of data breaches happen because of data that’s accessed and stored across various devices and locations.
Quantum computing, though still in its early stages, poses a potential risk to current encryption methods as it may bypass today’s computer programs. If quantum computers reach mainstream usability, today’s encryption standards could be rendered obsolete overnight, forcing businesses to adopt post-quantum cryptography.
Role of Human Error in Breaches

88% of data breaches are due to human error, often linked to weak passwords, misconfiguration, and phishing
Despite technological advancements, human error remains one of the biggest causes of data breaches. According to Stanford research, 88% of all data breaches happen at the hands of an employee. Many data incidents are linked to weak passwords, misconfigurations, and phishing scams. However, providing adequate cybersecurity training will help reduce data breach risks. In 2024, data from Statista showed that 45% of employees attended computer-based cybersecurity training compared to other forms. Businesses must prioritize ongoing cybersecurity education and access control policies to minimize risks.
Companies like Procurri help organisations mitigate risks by providing secure IT asset management and data protection strategies for end of life IT hardware, including full chain of custody reporting and secure, certified data erasure, ensuring that outdated infrastructure does not become an easy target for cybercriminals. As cyber threats evolve, businesses must stay proactive, leveraging both technology and human vigilance to protect sensitive information.
Financial Implications of Data Breaches
IBM’s Cost of a Data Breach report looked into data breaches around the world and found that globally, its average cost is $4.88 million. This number grew 10% from the previous year and highlights the growing cost of compromised data.

In the United States, the average cost of a data breach is $9.36 million, which is four times larger than the financial impact of data breaches in other countries. These are the factors that determine the cost of a breach:
- Sum of Losses: Amount lost in revenue, business, inflows, and customers
- According to IBM, organisations lose an average of $1.47 million during a data breach
- Breach Detection and Containment: Cost varies depending on the scale of the breach and the industry
- Breach containment and management can cost organisations $1.63 million on average
- Post-Breach Costs: Cost varies on the fines, legal fees, settlements, and miscellaneous varies depending on legal fees, settlements, and miscellaneous payments incurred after the breach is contained
- Breach victims stand to lose $1.35 million during the post-breach period
- Breach Notification Costs: Reporting data breaches to clients and external parties start at $430,000 and can reach millions
Regulatory Responses and Legal Implications
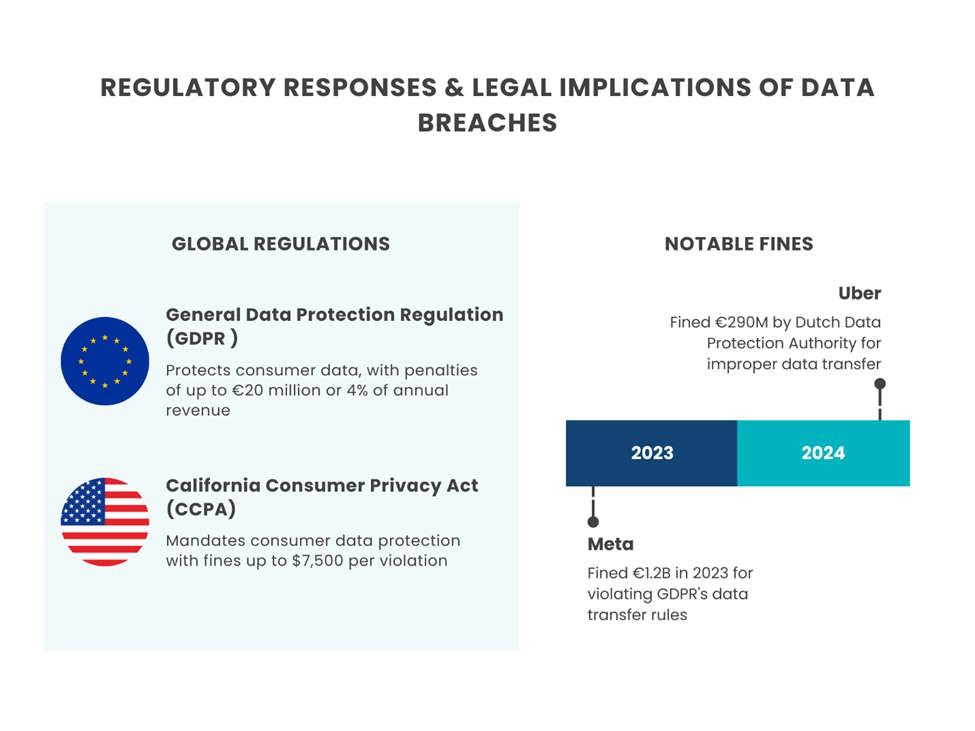
In response to escalating data breaches, global regulatory frameworks have been established to enforce stringent data protection standards. The European Union’s General Data Protection Regulation (GDPR) leads the effort to protect consumer data, imposing fines racking up to €20 million or 4% of a company’s global annual revenue for non-compliance. Similarly, the United States enforces regulations like the California Consumer Privacy Act (CCPA), which mandates consumer data protection with penalties reaching $7,500 per violation.
Non-compliance with these laws results in substantial financial repercussions. Uber was slapped with a €290 million penalty in August of 2024 by the Dutch Data Protection Authority. They were found to be improperly transferring driver data from the EU to the U.S., which was a clear violation of GDPR provisions. Similarly, in October 2023, Meta was fined €1.2 billion for failing to comply with GDPR’s data transfer rules.
Companies like Procurri offer comprehensive IT asset disposition and data destruction services, ensuring compliance with global data protection regulations for retired IT assets. By partnering with data security experts, organisations can mitigate risks associated with data breaches and avoid severe legal and financial penalties.
Mitigation Strategies and Best Practices
In today’s cybersecurity landscape, companies must be proactive in their defence strategies. The increasing sophistication of cyber threats, such as AI-driven phishing scams and deepfake-based social engineering, demands a multi-layered approach to security.
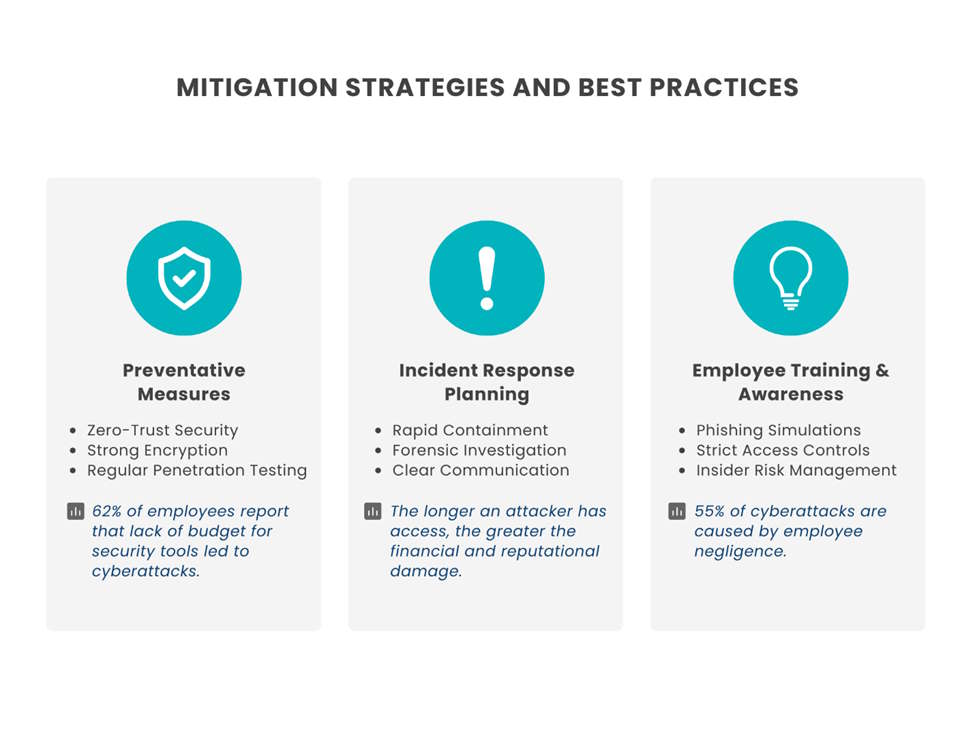
Preventive Measures
Organisations must start by minimizing vulnerabilities. This means implementing and investing in zero-trust architecture, where access to systems is never automatically granted, even to internal employees. CISO reports that 62% of employees found that not upgrading security tools due to lack of a budget has led to successful cyberattacks.
Encryption protocols should also extend beyond sensitive files to include emails and real-time communications. According to the cybersecurity company Cyble, regular penetration testing (simulating cyberattacks to identify weak points) can prevent a breach before it happens.
Incident Response Planning
Despite best efforts, breaches can still occur. Data resilience company Veeam underscores the importance of having a well-structured incident response plan (IRP) since this ensures that companies can act swiftly when a breach happens. The golden rule of response planning? Time is money. The longer an attacker has access, the greater the financial and reputational damage. Companies must establish clear response protocols, including immediate containment strategies, forensic analysis, and communication plans for affected customers.
Importance of Employee Training
Employee training is non-negotiable in preventing and managing data breaches. According to DTex’s Insider Risk Investigations Report, 12% of employees took sensitive data with them when they departed the company. Ponemon Institute’s report also says that 55% of attacks were caused by employee negligence. Cybercriminals exploit poor password hygiene, misplaced credentials, and unsuspecting employees clicking on malicious links. Regular phishing simulations, cybersecurity workshops, and mandatory security awareness programs significantly reduce these risks.
Companies like Procurri play a crucial role in ensuring businesses have secure, compliant IT asset management, reducing the risk of data exposure from outdated infrastructure. A strong cybersecurity posture is a strong competitive advantage.
Future Outlook for Data Breaches and Data Protection
Data breaches are anticipated to escalate in both frequency and sophistication. According to the FBI, cybercriminals are increasingly leveraging artificial intelligence (AI) to conduct more targeted and efficient attacks, including AI-generated voice and video phishing schemes. This evolution necessitates that organisations adopt advanced security measures to counteract these emerging threats.
In response to these challenges, the regulatory landscape is undergoing significant transformation. Several U.S. states have enacted comprehensive privacy laws effective this year, including Delaware, Iowa, Nebraska, New Hampshire, and New Jersey, with Minnesota and Tennessee set to follow in July, and Maryland in October. These laws impose stricter data protection requirements on businesses. Companies that fail to comply risk hefty fines, reputational damage, and loss of customer trust.
New technologies are quickly reshaping how companies protect their data. Zero-trust security models are becoming a necessity, with data from Statista noting that 61% of respondents agree. Instead of assuming internal users can be trusted, these systems require continuous verification before granting access, making it harder for cybercriminals to move without being detected.

AI adoption saves up to $2.2 million in breach management efforts
Meanwhile, AI-driven security tools are stepping up as a frontline defence. These systems actively predict and prevent attacks by analysing patterns in real time. They can flag unusual activity, like a login from an unfamiliar location, and shut it down before any damage is done. According to IBM, AI adoption saves up to $2.2 million in breach management efforts.
Key Takeaways
AI-powered cyberattacks, from deepfake fraud to AI-generated phishing, are outpacing traditional security measures, forcing businesses to adopt proactive defences. Industries handling sensitive data—healthcare, finance, and government—are prime targets for ransomware, phishing, and supply chain attacks.
Governments are tightening data protection laws, with regulations like the EU AI Act and GDPR imposing steep fines for non-compliance. To stay ahead, companies are deploying zero-trust security models and AI-driven threat detection, which can analyse anomalies and halt cyberattacks in real-time.
Prevention is far cheaper than damage control. Organisations must prioritize risk mitigation and compliance to safeguard both data and reputation. Secure IT asset management plays a crucial role in reducing exposure from outdated infrastructure, ensuring businesses remain resilient against evolving threats.
